Step-by-Step: Crack CFA or CPA Exams with an Online BCom Degree in India (Prep Tips & Success Rates)
Choosing the right undergraduate degree is the first and most important step for students who dream of building a successful career in finance or accounting. Bachelor of Commerce (B.Com) is one of the most versatile and globally accepted degrees that builds a strong foundation in commerce, finance, and business principles.
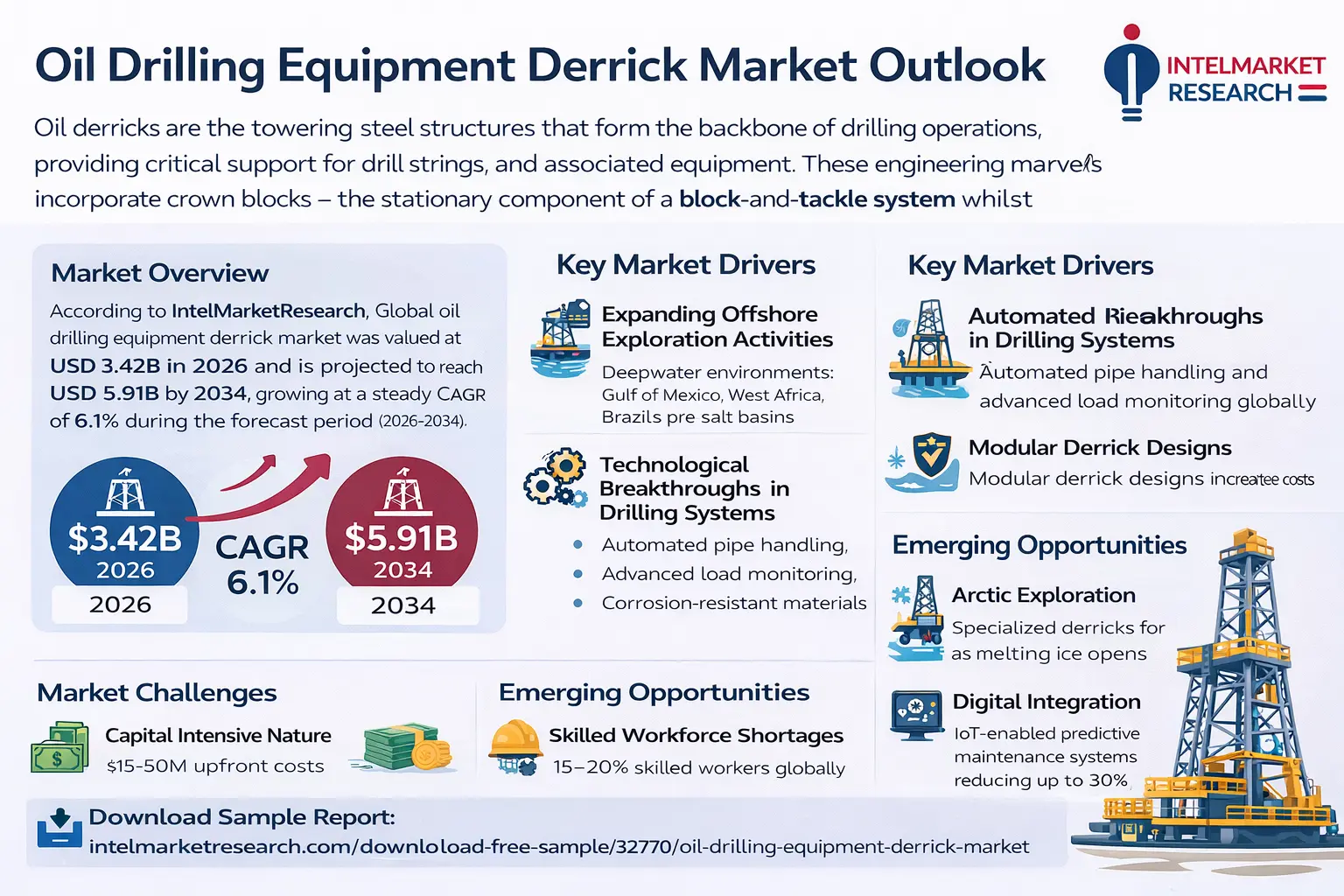
Marwadi University Online offers a UGC-entitled 3-year Online B.Com degree designed especially for students who want flexibility without compromising on academic quality. The program covers core subjects like Financial Accounting, Corporate Finance, Business Economics, Cost Accounting, Taxation, and Auditing, which are directly aligned with the syllabus of CFA and CPA exams.
For students aiming to crack CFA (Chartered Financial Analyst) or CPA (Certified Public Accountant), a strong conceptual base is non-negotiable. An online B.Com from Marwadi University helps students understand finance and accounting concepts step by step, making professional exam preparation more structured and less stressful.
What makes Marwadi University Online stand out is its industry-relevant curriculum, experienced faculty, and learner-friendly digital platform. Students can study at their own pace, revise concepts multiple times, and simultaneously prepare for competitive global certifications like CFA and CPA.
A B.Com graduate from Marwadi University Online is not limited to just one career path. With the right guidance and preparation, students can pursue CFA, CPA, CA, CS, or even move into roles like Financial Analyst, Investment Banker, Auditor, Risk Consultant, or Global Accounting Professional.
This blog explains how an Online B.Com from Marwadi University supports CFA and CPA preparation, why it is a smart choice for working students and aspirants, and how you can plan your journey step by step toward international finance certifications.
What is a Chartered Financial Analyst (CFA)?
The Chartered Financial Analyst (CFA) is one of the most respected and globally recognised certifications in the finance industry. Offered by the CFA Institute (USA), this qualification proves your expertise in investment management, financial analysis, equity research, and portfolio management.
For students pursuing an Online B.Com from Marwadi University, CFA acts as a career accelerator. It adds international credibility to your degree and opens doors to high-growth finance roles—not just in India, but worldwide.
CFA professionals are trusted with big financial decisions, and that trust brings strong career growth, respect, and long-term stability.
CFA Exam Eligibility (Perfect Fit for Online B.Com Students)
The CFA Institute has clear eligibility rules, and the good news is Online B.Com students from Marwadi University fit in well.
You can register for the CFA exam if you meet any one of the following conditions:
You have completed a Bachelor’s degree (including Online B.Com from a UGC-recognised university like Marwadi University)
You are in the final year of your B.Com degree
You have 4 years of relevant professional work experience
You must have English proficiency and a valid passport
This flexibility allows Marwadi University Online B.Com students to start CFA preparation early, without waiting years after graduation.
CFA Exam Structure (What You Need to Prepare For)
The CFA exam has three levels, and each level builds your confidence and expertise step by step:
CFA Level I – Foundation Stage
Focuses on basic finance, economics, accounting, and ethics
Pass rate: 40%–45%
Ideal to attempt during or soon after your Online B.Com
CFA Level II – Application Stage
Tests real-world application of financial concepts
Pass rate: 40%–50%
Requires deeper understanding and practice
CFA Level III – Strategy & Leadership Stage
Focuses on portfolio management and wealth planning
Includes essay-type questions
Pass rate: 50%–55%
CFA is challenging, but not impossible. With strong self-study habits, discipline, and the flexible learning environment of Marwadi University’s Online B.Com, students can balance degree studies and CFA preparation effectively.
CFA Career & Salary in India
A CFA certification significantly boosts your earning potential and career scope.
Popular CFA Job Roles:
Financial Analyst
Investment Banker
Portfolio Manager
Equity Research Analyst
Financial Consultant
Average CFA Salary in India:
Entry to mid-level: ₹6–8 LPA
Experienced professionals: ₹12–20 LPA or more
When combined with an Online B.Com from Marwadi University, CFA gives you both academic foundation + global professional recognition a combination recruiters value deeply.
What is a Certified Public Accountant (CPA)?
A Certified Public Accountant (CPA) is one of the most respected global accounting qualifications, especially for students who want international careers in accounting, auditing, finance, and taxation.
For Indian students, CPA is awarded by the American Institute of Certified Public Accountants (AICPA) and has become increasingly popular since 2021, as more global companies started hiring CPA-qualified professionals from India.
If you are pursuing an Online BCom degree from Marwadi University, CPA can be a powerful next step to build a global accounting career without leaving India.
Why CPA Makes Sense for Marwadi University Online BCom Students
Many students choose Marwadi University Online BCom because it offers:
Flexibility to study from anywhere
Strong foundation in accounting and finance
Time to prepare for professional courses alongside graduation
This flexibility is ideal for CPA aspirants because:
You can study for CPA along with your Online BCom
Your degree builds the core accounting knowledge needed for CPA
You save time and cost compared to traditional pathways
For students dreaming of international exposure, higher salary, and global recognition, CPA is a smart choice.
CPA Exam Eligibility (Explained Simply)
To appear for the CPA exam, candidates generally need:
A Bachelor’s degree in Accounting or a related field (like Online BCom from Marwadi University)
A total of 150 credit hours (this can be completed through graduation & additional qualifications)
1–2 years of relevant work experience (depends on the U.S. state board)
Many Indian students start CPA preparation during or immediately after Online BCom, and complete remaining requirements gradually.
CPA Examination Structure
The CPA exam must be cleared within an 18-month window and consists of four sections:
AUD: Auditing & Attestation
Focuses on audit processes, ethics, and compliance.
BEC: Business Environment & Concepts
Covers business strategy, economics, and financial management.
FAR: Financial Accounting & Reporting
The most detailed section, based on accounting standards and reporting.
REG: Regulation
Includes taxation, business laws, and ethics.
With proper planning, Online BCom students from Marwadi University can prepare step-by-step without academic pressure.
CPA Registration Process (Step-by-Step)
The CPA registration process is completely online, making it convenient for Indian students:
Apply for international credential evaluation
Submit academic documents to NASBA
Receive eligibility confirmation
Register for exam sections and pay fees
Schedule and appear for exams
This structured process allows Online BCom students to plan their CPA journey confidently.
Career Opportunities After CPA
After becoming a CPA, students can work in:
Public accounting firms
MNCs and global corporations
Consulting firms
Government and regulatory bodies
Non-profit organizations
Popular job roles include:
Financial Analyst
Auditor
Tax Consultant
Accounting Manager
Chief Financial Officer (CFO)
CPA Salary in India (Reality Check)
Due to high demand and limited qualified professionals, CPAs enjoy strong salary growth in India:
Entry-level CPA: ₹6–8 LPA
Mid-level CPA: ₹12–20 LPA
Senior roles: Even higher with experience
For students from Marwadi University Online BCom, CPA opens doors to financial stability, respect, and global career growth.
Why CPA & Online BCom is a Smart Combination
Choosing an Online BCom from Marwadi University while preparing for CPA allows students to:
Learn at their own pace
Avoid career gaps
Build international credentials early
Reduce overall education cost
It’s not just about exams it’s about building a future that gives you confidence, freedom, and recognition.
CFA vs CPA: Which One Should You Choose After Online BCom?
If you are pursuing an Online BCom from Marwadi University and planning a professional certification, CFA and CPA are two of the most respected global options.
Both offer strong career growth, but their career paths are very different.
Understanding this difference early can save you time, money, and confusion.
Key Differences Between CFA and CPA
Aspect
CFA
CPA
Area of Focus
Focuses on investment analysis, portfolio management, equity research, and ethics
Focuses on accounting, auditing, taxation, compliance, and financial reporting
Best Suited For
Students interested in finance, stock markets, investments, and wealth management
Students interested in accounts, taxation, audits, and corporate finance roles
Job Roles
Financial Analyst, Investment Banker, Portfolio Manager, Equity Research Analyst
Accountant, Auditor, Tax Consultant, Financial Advisor, Accounting Manager
Exam Structure
3 levels (Level I, II, III) cleared sequentially
4 sections (AUD, BEC, FAR, REG) cleared within 18 months
Professional Body
Conducted by the CFA Institute (USA)
Certified by AICPA (USA)
Skillset Required
Strong analytical thinking, quantitative skills, and financial modeling
Strong accounting knowledge, taxation laws, and compliance understanding
Difficulty Level
Conceptually intense with long study hours
Technically detailed but structured
Salary Potential
Higher earning potential in investment and leadership finance roles
Stable and competitive salaries in accounting, audit, and corporate roles
CFA or CPA – Which Is Better for You?
There is no “better” certification, only the right one for your career goal.
Choose CFA if you:
Love finance, numbers, and market analysis
Want to work in investments, asset management, or global finance firms
Are ready for deep analytical and long-term study
Step-by-Step: Crack CFA or CPA Exams with an Online BCom Degree in India (Prep Tips & Success Rates)
Choosing the right undergraduate degree is the first and most important step for students who dream of building a successful career in finance or accounting. Bachelor of Commerce (B.Com) is one of the most versatile and globally accepted degrees that builds a strong foundation in commerce, finance, and business principles.
Marwadi University Online offers a UGC-entitled 3-year Online B.Com degree designed especially for students who want flexibility without compromising on academic quality. The program covers core subjects like Financial Accounting, Corporate Finance, Business Economics, Cost Accounting, Taxation, and Auditing, which are directly aligned with the syllabus of CFA and CPA exams.
For students aiming to crack CFA (Chartered Financial Analyst) or CPA (Certified Public Accountant), a strong conceptual base is non-negotiable. An online B.Com from Marwadi University helps students understand finance and accounting concepts step by step, making professional exam preparation more structured and less stressful.
What makes Marwadi University Online stand out is its industry-relevant curriculum, experienced faculty, and learner-friendly digital platform. Students can study at their own pace, revise concepts multiple times, and simultaneously prepare for competitive global certifications like CFA and CPA.
A B.Com graduate from Marwadi University Online is not limited to just one career path. With the right guidance and preparation, students can pursue CFA, CPA, CA, CS, or even move into roles like Financial Analyst, Investment Banker, Auditor, Risk Consultant, or Global Accounting Professional.
This blog explains how an Online B.Com from Marwadi University supports CFA and CPA preparation, why it is a smart choice for working students and aspirants, and how you can plan your journey step by step toward international finance certifications.
What is a Chartered Financial Analyst (CFA)?
The Chartered Financial Analyst (CFA) is one of the most respected and globally recognised certifications in the finance industry. Offered by the CFA Institute (USA), this qualification proves your expertise in investment management, financial analysis, equity research, and portfolio management.
For students pursuing an Online B.Com from Marwadi University, CFA acts as a career accelerator. It adds international credibility to your degree and opens doors to high-growth finance roles—not just in India, but worldwide.
CFA professionals are trusted with big financial decisions, and that trust brings strong career growth, respect, and long-term stability.
CFA Exam Eligibility (Perfect Fit for Online B.Com Students)
The CFA Institute has clear eligibility rules, and the good news is Online B.Com students from Marwadi University fit in well.
You can register for the CFA exam if you meet any one of the following conditions:
You have completed a Bachelor’s degree (including Online B.Com from a UGC-recognised university like Marwadi University)
You are in the final year of your B.Com degree
You have 4 years of relevant professional work experience
You must have English proficiency and a valid passport
This flexibility allows Marwadi University Online B.Com students to start CFA preparation early, without waiting years after graduation.
CFA Exam Structure (What You Need to Prepare For)
The CFA exam has three levels, and each level builds your confidence and expertise step by step:
CFA Level I – Foundation Stage
Focuses on basic finance, economics, accounting, and ethics
Pass rate: 40%–45%
Ideal to attempt during or soon after your Online B.Com
CFA Level II – Application Stage
Tests real-world application of financial concepts
Pass rate: 40%–50%
Requires deeper understanding and practice
CFA Level III – Strategy & Leadership Stage
Focuses on portfolio management and wealth planning
Includes essay-type questions
Pass rate: 50%–55%
CFA is challenging, but not impossible. With strong self-study habits, discipline, and the flexible learning environment of Marwadi University’s Online B.Com, students can balance degree studies and CFA preparation effectively.
CFA Career & Salary in India
A CFA certification significantly boosts your earning potential and career scope.
Popular CFA Job Roles:
Financial Analyst
Investment Banker
Portfolio Manager
Equity Research Analyst
Financial Consultant
Average CFA Salary in India:
Entry to mid-level: ₹6–8 LPA
Experienced professionals: ₹12–20 LPA or more
When combined with an Online B.Com from Marwadi University, CFA gives you both academic foundation + global professional recognition a combination recruiters value deeply.
What is a Certified Public Accountant (CPA)?
A Certified Public Accountant (CPA) is one of the most respected global accounting qualifications, especially for students who want international careers in accounting, auditing, finance, and taxation.
For Indian students, CPA is awarded by the American Institute of Certified Public Accountants (AICPA) and has become increasingly popular since 2021, as more global companies started hiring CPA-qualified professionals from India.
If you are pursuing an Online BCom degree from Marwadi University, CPA can be a powerful next step to build a global accounting career without leaving India.
Why CPA Makes Sense for Marwadi University Online BCom Students
Many students choose Marwadi University Online BCom because it offers:
Flexibility to study from anywhere
Strong foundation in accounting and finance
Time to prepare for professional courses alongside graduation
This flexibility is ideal for CPA aspirants because:
You can study for CPA along with your Online BCom
Your degree builds the core accounting knowledge needed for CPA
You save time and cost compared to traditional pathways
For students dreaming of international exposure, higher salary, and global recognition, CPA is a smart choice.
CPA Exam Eligibility (Explained Simply)
To appear for the CPA exam, candidates generally need:
A Bachelor’s degree in Accounting or a related field (like Online BCom from Marwadi University)
A total of 150 credit hours (this can be completed through graduation & additional qualifications)
1–2 years of relevant work experience (depends on the U.S. state board)
Many Indian students start CPA preparation during or immediately after Online BCom, and complete remaining requirements gradually.
CPA Examination Structure
The CPA exam must be cleared within an 18-month window and consists of four sections:
AUD: Auditing & Attestation
Focuses on audit processes, ethics, and compliance.
BEC: Business Environment & Concepts
Covers business strategy, economics, and financial management.
FAR: Financial Accounting & Reporting
The most detailed section, based on accounting standards and reporting.
REG: Regulation
Includes taxation, business laws, and ethics.
With proper planning, Online BCom students from Marwadi University can prepare step-by-step without academic pressure.
CPA Registration Process (Step-by-Step)
The CPA registration process is completely online, making it convenient for Indian students:
Apply for international credential evaluation
Submit academic documents to NASBA
Receive eligibility confirmation
Register for exam sections and pay fees
Schedule and appear for exams
This structured process allows Online BCom students to plan their CPA journey confidently.
Career Opportunities After CPA
After becoming a CPA, students can work in:
Public accounting firms
MNCs and global corporations
Consulting firms
Government and regulatory bodies
Non-profit organizations
Popular job roles include:
Financial Analyst
Auditor
Tax Consultant
Accounting Manager
Chief Financial Officer (CFO)
CPA Salary in India (Reality Check)
Due to high demand and limited qualified professionals, CPAs enjoy strong salary growth in India:
Entry-level CPA: ₹6–8 LPA
Mid-level CPA: ₹12–20 LPA
Senior roles: Even higher with experience
For students from Marwadi University Online BCom, CPA opens doors to financial stability, respect, and global career growth.
Why CPA & Online BCom is a Smart Combination
Choosing an Online BCom from Marwadi University while preparing for CPA allows students to:
Learn at their own pace
Avoid career gaps
Build international credentials early
Reduce overall education cost
It’s not just about exams it’s about building a future that gives you confidence, freedom, and recognition.
CFA vs CPA: Which One Should You Choose After Online BCom?
If you are pursuing an Online BCom from Marwadi University and planning a professional certification, CFA and CPA are two of the most respected global options.
Both offer strong career growth, but their career paths are very different.
Understanding this difference early can save you time, money, and confusion.
Key Differences Between CFA and CPA
Aspect
CFA
CPA
Area of Focus
Focuses on investment analysis, portfolio management, equity research, and ethics
Focuses on accounting, auditing, taxation, compliance, and financial reporting
Best Suited For
Students interested in finance, stock markets, investments, and wealth management
Students interested in accounts, taxation, audits, and corporate finance roles
Job Roles
Financial Analyst, Investment Banker, Portfolio Manager, Equity Research Analyst
Accountant, Auditor, Tax Consultant, Financial Advisor, Accounting Manager
Exam Structure
3 levels (Level I, II, III) cleared sequentially
4 sections (AUD, BEC, FAR, REG) cleared within 18 months
Professional Body
Conducted by the CFA Institute (USA)
Certified by AICPA (USA)
Skillset Required
Strong analytical thinking, quantitative skills, and financial modeling
Strong accounting knowledge, taxation laws, and compliance understanding
Difficulty Level
Conceptually intense with long study hours
Technically detailed but structured
Salary Potential
Higher earning potential in investment and leadership finance roles
Stable and competitive salaries in accounting, audit, and corporate roles
CFA or CPA – Which Is Better for You?
There is no “better” certification, only the right one for your career goal.
Choose CFA if you:
Love finance, numbers, and market analysis
Want to work in investments, asset management, or global finance firms
Are ready for deep analytical and long-term study